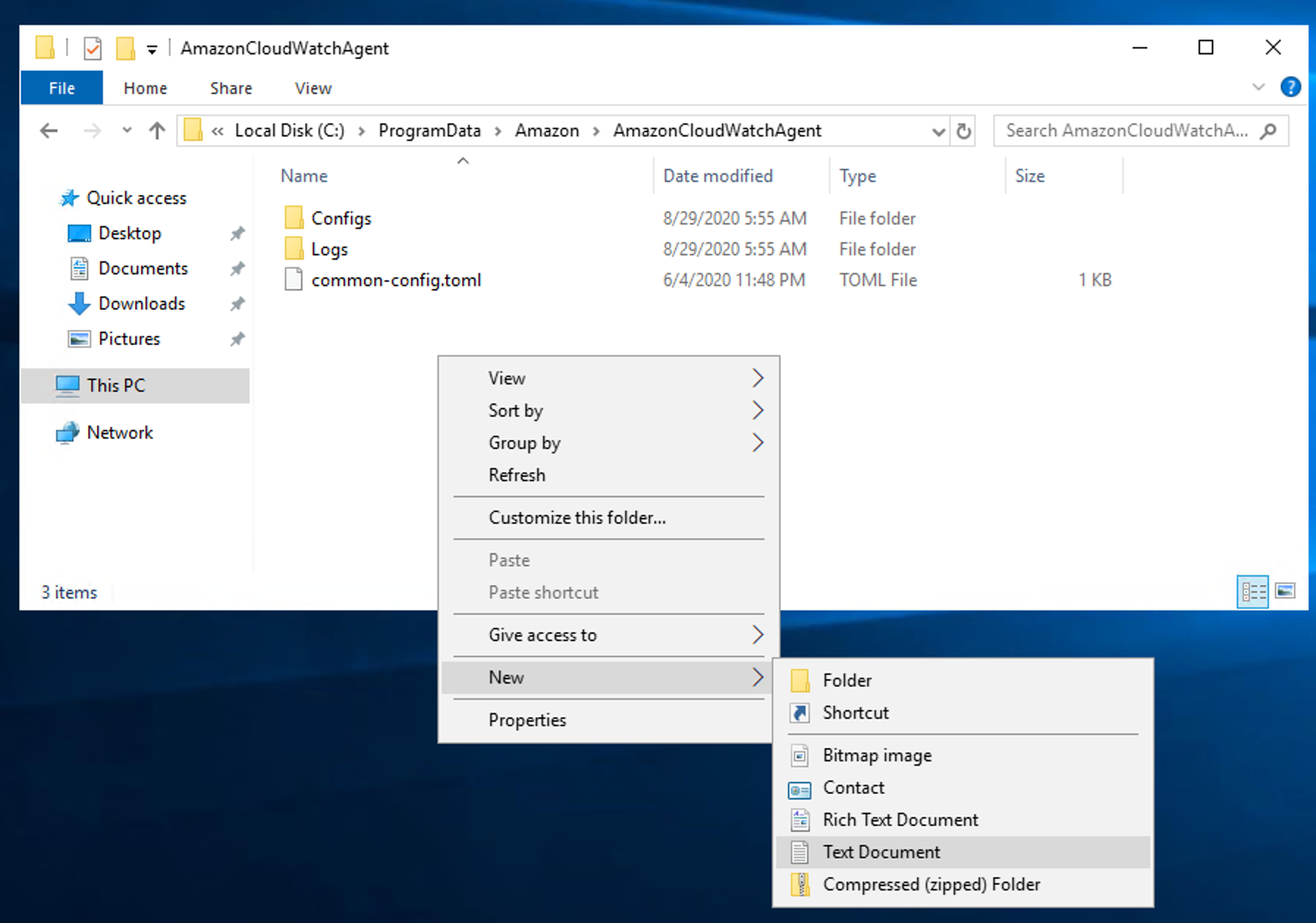
AWS documentation is simple but has many links which redirect users to various other documents to deploy application on AWS EC2 using code deploy and that seems to be confusing sometimes That is whyEMR Deployment Instructions The following steps enable Tecton to access your control plane account to manage AWS and Spark resources These instructions assume you are using EMR as the Spark provider If you are using Databricks, please see the Databricks deployment instructions Terraform Templates AmazonSSMManagedInstanceCore This policy enables the EC2 instance to read parameters stored in the SSM parameter store and to have them registered under the SSM managed instances, so you can Run Commands against it Ensure that the SSM agent is installed in this EC2 instance Install the Amazon CloudWatch Agent on an EC2 instance ^
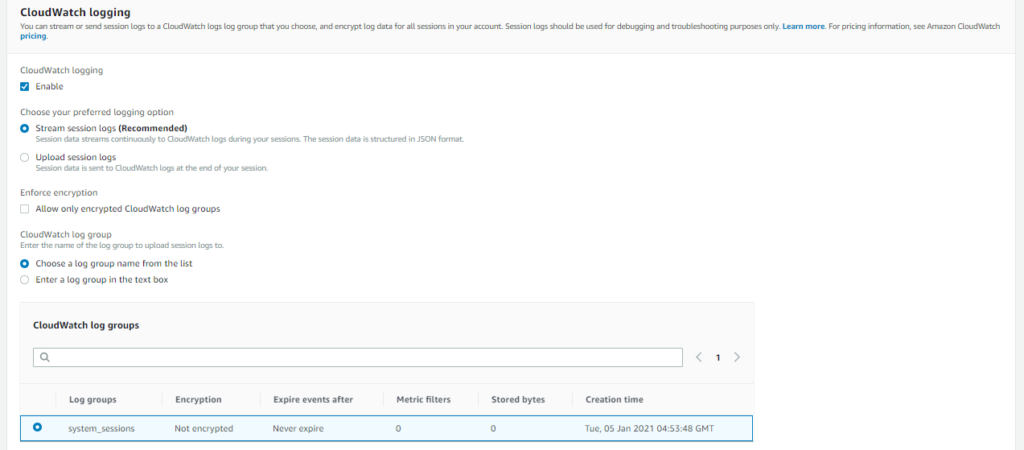
Using Aws Systems Manager Session Manager Kernel Talks
Amazonssmmanagedinstancecore json
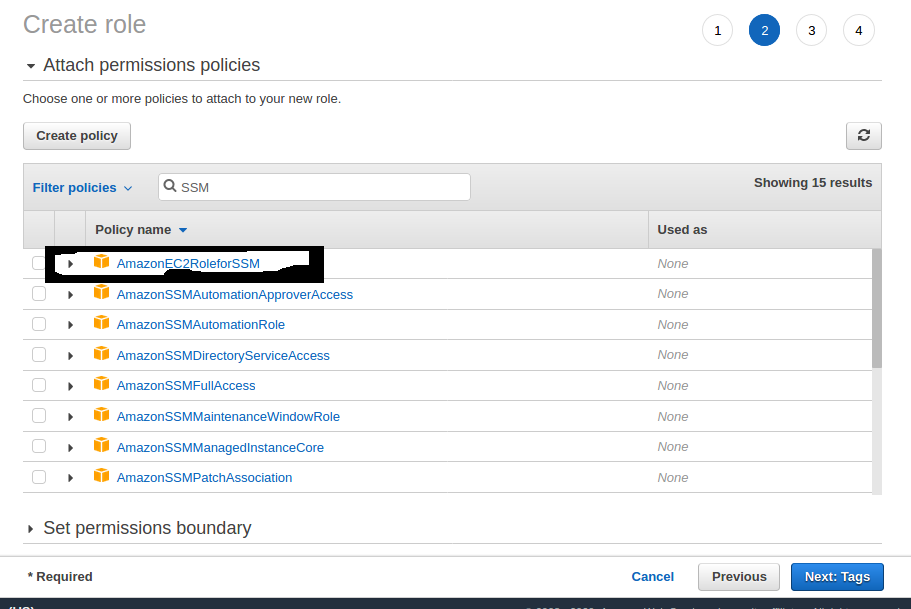
Amazonssmmanagedinstancecore json- IAM Role To enable automatic scaling and backups on the VSA access node, select the IAM role that has both the AmazonSSMManagedInstanceCore managed policy and the amazon_permission_backup_restorejson file attached You can find the policy in the AWS console at arnawsiamawspolicy/AmazonSSMManagedInstanceCoreCloudFormation, Terraform, and AWS CLI Templates Configuration to create an IAM role for EC2 instances to access to AWS Systems Manager (SSM) services, with the least permissions required




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog
AWS Session Manager with Enhanced SSH and SCP Capability A year ago, new features in the AWS Systems Manager Session Manager were uncovered by AWS (Amazon Web Services) Now users can directly tunnel Secure Shell (SSH) and Secure Copy (SCP) connections from local clients without needing an AWS management consoleLastly, you'll need to import the required libraries by running the following command in terminal pip install awscdkcore awscdkcloudformation_include awscdkawss3 awscdkawslambda awsJSON Syntax Rules JSON syntax is derived from JavaScript object notation syntax Data is in name/value pairs Data is separated by commas Curly braces hold
Set deployment environment variable to local, staging or production AWS recently enhanced its Systems Manager offering with shell access to EC2 instances and then they enhanced it further with SSH tunnel supportWith these improvements, it's now possible to improve your application's security posture while reducing it's operational costs and simplifying setup/maintenance configuration a JSON file must be supplied which defines the logs to be collected along with which log group they should be streamed to We also provide AmazonSSMManagedInstanceCore policy in order that we can start a session in the instance using a Session Manager shell (more info later) a log group;
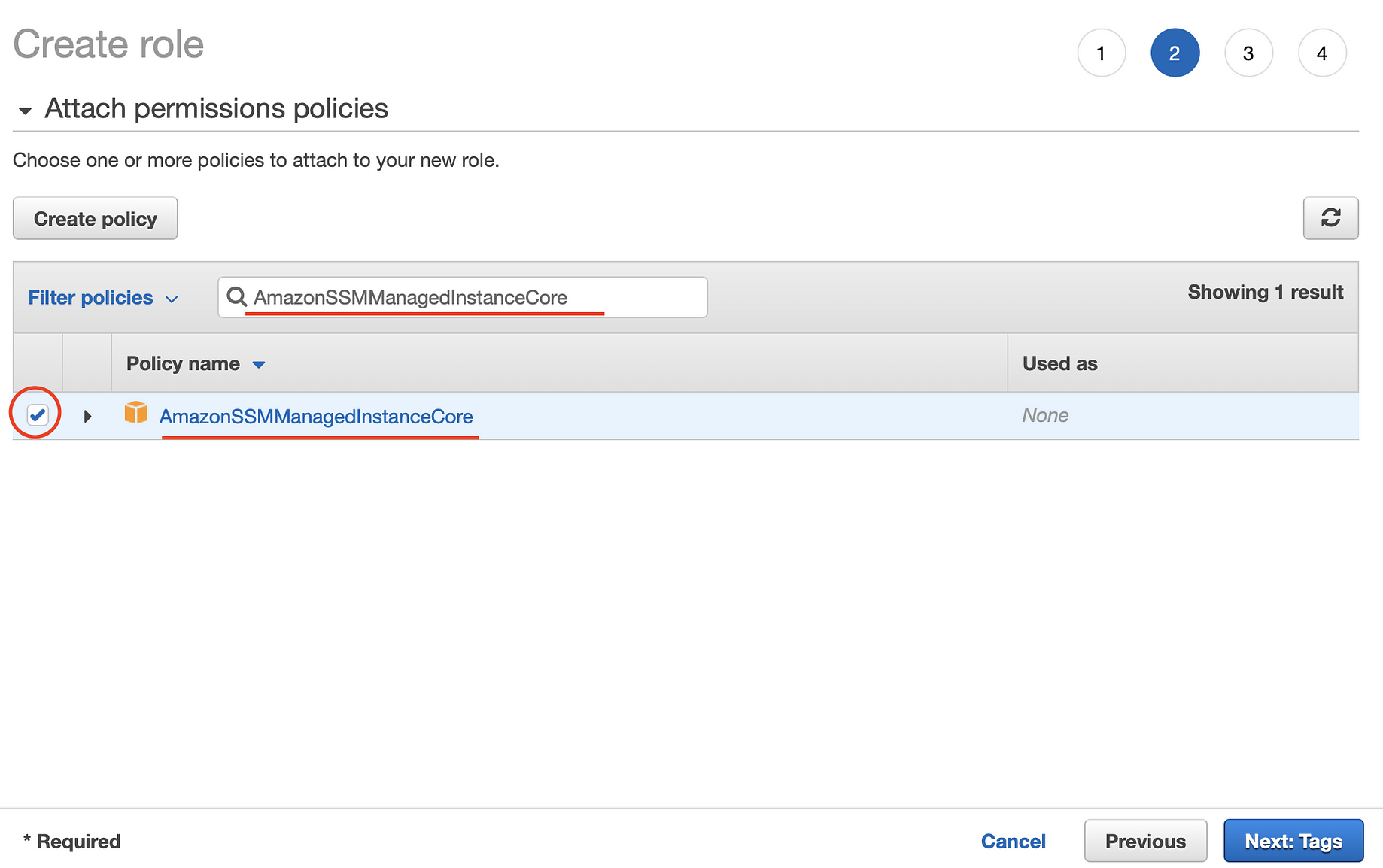
resource " aws_iam_role_policy_attachment " " AmazonSSMManagedInstanceCore " {role = aws_iam_role this name policy_arn = " arnawsiamawspolicy/AmazonSSMManagedInstanceCore "} resource " aws_iam_role_policy_attachment " " CloudWatchAgentServerPolicy " {role = aws_iam_role this Automation Documents A Systems Manager Automation document defines the actions that Systems Manager performs on your managed instances and other AWS resources when an automation execution runs A document contains one or more steps that run in sequential order Each step is built around a single action IAM Role To enable automatic scaling and backups on the VSA access node, select the IAM role that has both the AmazonSSMManagedInstanceCore managed policy and the amazon_permission_backup_restorejson file attached
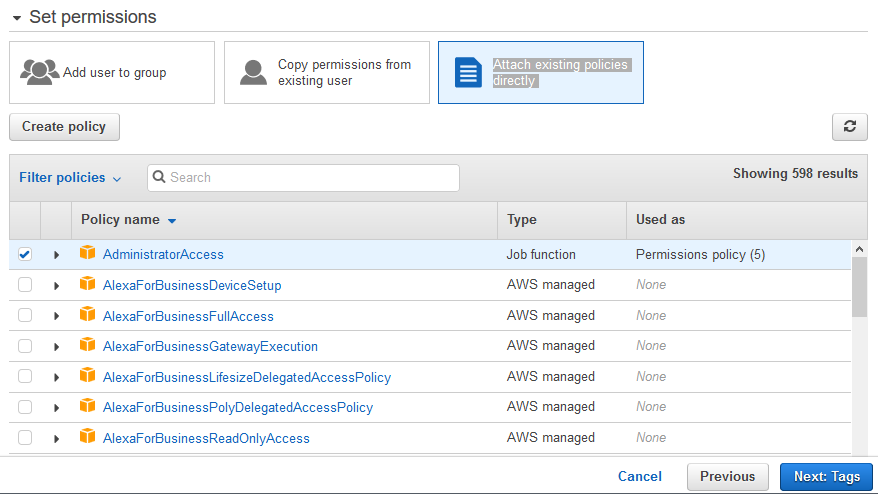



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise
IAM requirements differ between project to project Depending on the complexity, we could create the IAM resources with Terraform in the relevant layer However, having the IAM resources dynamically create within its own module, or even combining them with their resource counterparts, gives us great powerThe first policy, AmazonSSMManagedInstanceCore, allows an instance to use AWS Systems Manager service core functionality Depending on your operations plan, you might need permissions represented in one or more of the other three policiesUse euwest1 for the region and json for the output format Next run the command aws ssm startsession –target {instanceid} –documentname AWSStartPortForwardingSession –parameters portNumber="33",localPortNumber="567" Replace {instanceid} with the actual Instance ID of the EC2 instance
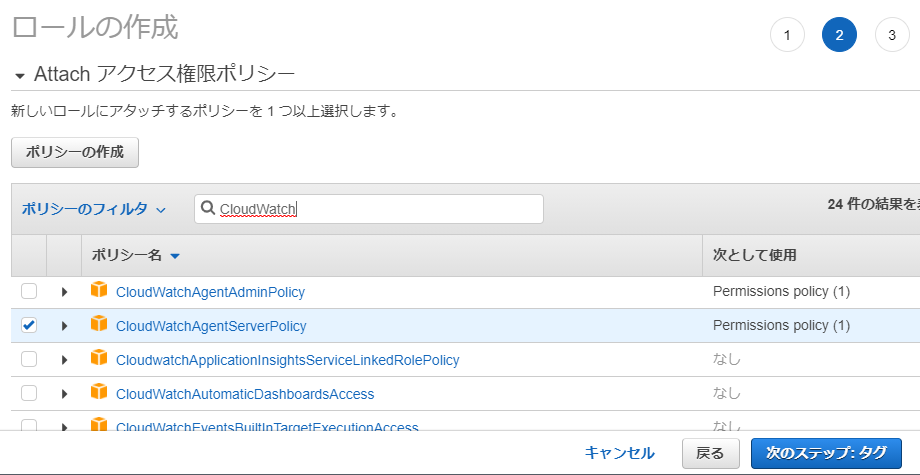



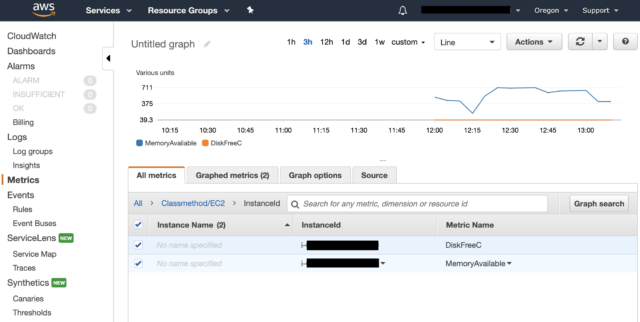
Aws Link Memory Usage Of Ubuntu Ec2 Instance To Cloudwatch




Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn
Adding Session Manager permissions to an existing instance profile Follow these steps to embed Session Manager permissions in an existing AWS Identity and Access Management (IAM) instance profile that doesn't rely on the AWSprovided default policy AmazonSSMManagedInstanceCore for instance permissions In this section we will talk about Identity and Access Management – IAM in short I will show you an example of using AWS CDK to create IAM roles with C# and extending our current solution so that an IAM Role is ready with the correct permission to Easy EC2 SSM with Pulumi in Typescript After watching this talk from Luke Hoban, I wanted to give it a spinHoban's analogy of current tools as Assembly language of the could, that will eventually be surpassed by a programming language is pretty attractive




Backup And Recovery Of Sap Hana Database Directly To Aws S3 Bucket Using Aws Backint Agent Part I




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Stack Over Cloud
The open source version of the Amazon ECS developer guide You can submit feedback &I'm using Terraform to create IAM and EC2 as below I want to attach a role named ec2_role to the EC2 instance profile But it seems it only can attach one that created by aws_iam_instance_profile resource "aws_instance" "this" { # output = json region = apsoutheast2 session output = json region = apsoutheast2 𝜆 cat aws/credentials default aws_access_key_id = ASIANPOWERHOUSEBLAHBLAH NOTE IAM role for EC2 instance need to have AmazonSSMManagedInstanceCore policy
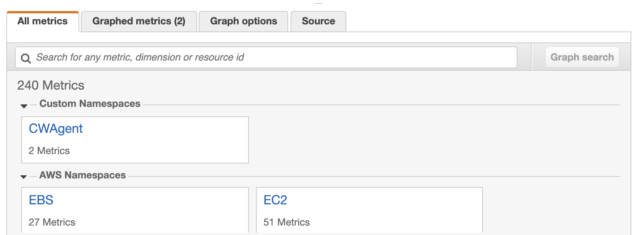



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio




Use Systems Manager Session Manager With Stax Networks Vpcs Stax Docs
For publishing any of the logs or metrics from EC2 to SumoLogic we need to have the access_id and access_key of SumoLogic Two differentAutoscalinglambdats GitHub Gist instantly share code, notes, and snippets Create an IAM role in AWS called awsKeysjson with following permissions AmazonEC2FullAccess, AmazonSQSFullAccess, AmazonEC2RoleforSSM, AmazonS3FullAccess, AmazonSSMManagedInstanceCore, AmazonSSMFullAccess, An inline policy that allows IAM readwrite;



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio
Before we deploy the web application, we need to create an Amazon EC2 instance and supporting resources In this module, we'll create the new AWS CDK app, install the dependencies for our resources, and finally define an Amazon EC2 instance, a security group with inbound access, and an IAM instance profile Then create the role and verify aws iam createrole rolename $ROLE_NAME assumerolepolicydocument file//ssmtrustpolicyjson aws iam attachrolepolicy rolename $ROLE_NAME policyarn arnawsiamawspolicy/AmazonSSMManagedInstanceCore aws iam attachrolepolicy rolename $ROLE_NAME policyarn SUSE Linux Enterprise Server as ECS Anywhere Host On AWS announced the availability of ECS Anywhere There is also a home lab setup guide ECS is a container orchestration service and with the addition of "Anywhere" the service can now reach into your Data Center to orchestrate your containerized applications




1 2 Ec2 Instance Profile Ec2 Image Builder Workshop




Shipping Aws Ec2 Logs To Cloudwatch With The Cloudwatch Agent Tom Gregory
If you want the role to be able to use the arnawsiamawspolicy/AmazonSSMManagedInstanceCore policy and also be able to assume the arnawsiamrole/s3role role (although it would be more normal to give the permissions directly to the role rather than use role chaining and if this involves cross account After the Part 1 post, which specifically explaining configuration with packer, on this part, I'll write more about Terraform and AWS CodebuildECS gMSA Workshop > ECS Cluster > Cluster Domain Join Attach policy AmazonSSMManagedInstanceCore Associate the domain join document Wait for the instances to join the domain Create AD security group Create the credspec document Store the credspec as Systems Manager parameter



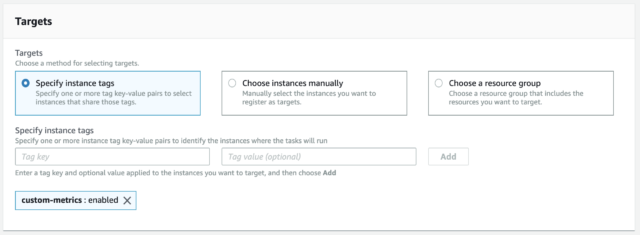
Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn




How To Simplify Microsoft Sql Server Backup Using Aws Backup And Vss Aws Storage Blog
Despite its shortcomings, JSON is the most common format for APIs on the web so we need a way to work with it in Java Jackson is one of the most popular Java JSON libraries, and is the one I use most frequently In this post I'll pick a fairly complex JSON document and three queries which I want to make using Jackson AWS Systems Manager need access to AWS resources to install AWS Backint Agent, for this managed policy AmazonSSMManagedInstanceCore needs to be attached to the IAM role Click on Json AWS IAM Console Paste the below policy and replace the required fields and Click on Review Policy { "Version" ""Requests for changes by submitting issues in this repo or by making proposed changes &




Automating Amazon Cloudwatch Alarms With Aws Systems Manager Aws Management Governance Blog




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com
Add the following modulesto the dependencies "@awscdk/core" "*", "@awscdk/awsec2" "*", "@awscdk/awsiam" "*", This is an optional step, but go ahead and run "npm install" in the root directory of your project This will download the dependencies and give you intellisense which comes very handy I was recently tasked with finding a solution to migrate the Application Logs of an EC2 instance to CloudWatch, then export the logs to S3 using automation In order to make this walkthrough "short" and easy to read, I have divided it into two articles The most useful information can be found in the one which starts with 'TOE' and is followed by a timestamp This directory contains the entire log of the phase, the console output, the yaml document of the specific component as well as json outputs The image below, shows the consolelog of the test phase As you can notice, it worked as



The Cloud Infrastructure Management Using Aws Systems Manager Ssm By Crishantha Nanayakkara Medium
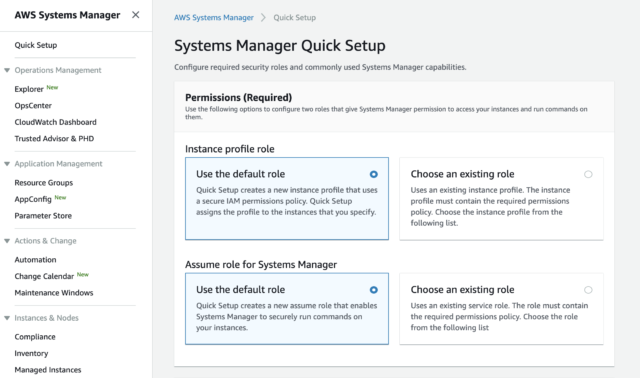



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio
代わりにこれからは、新しいポリシー AmazonSSMManagedInstanceCore をベースに、ゼロからカスタムポリシーを作ること $ diff u AmazonEC2RoleforSSMjson AmazonSSMManagedInstanceCorejson AmazonEC2RoleforSSMjson 0900 AmazonSSMManagedInstanceCorejson 19 2 In the Resources section of your template, for the resource of type AWSIAMRole, set Ref to the parameters that you created in step 1 For this example, these are the awsExampleManagedPolicyParameterOne and awsExampleManagedPolicyParameterTwo parameters See the following JSON and YAML examples I am using EC2 windows I have installed the cloudwatch agent and created the configjson I started the agent The windows logs are being written to cloudwatch but the application logs are not I am getting logsMetric Access is denied in the CLoudwatchagent logs I have application logs under C\Apachelogs, C\MongoLogs
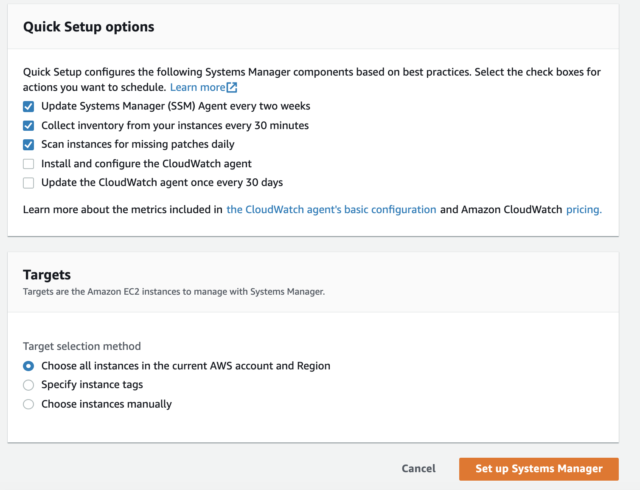



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio




Can T Connect To Windows Ec2 Instance Built By Packer Via Ssm Agent Server Fault
If you're using an onpremises access node (MediaAgent), then in the AWS console, you must configure an IAM user with the AmazonSSMManagedInstanceCore policy attached and the restricted backuprestore JSON file attached13 EC2 Instance Profile Intro Because EC2 Image Builder uses EC2 instances to created an AMI, you need to use an EC2 Instance ProfileWhen you use a role, you don't have to distribute longterm credentials (such as a user name and password or access keys) to an EC2 instance




Steve Roberts Noise




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Stack Over Cloud



Cool Assessment Terraform Pentestportal Iam Tf At Develop Cisagov Cool Assessment Terraform Github




Lightsailにssmエージェントを導入する Qiita




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise



How To Run Commands Remotely On An Ec2 Instance Using Aws Systems Manager By Workfall The Workfall Blog Medium



Noise The Collective Thoughts Of The Interwebz Page 271




Uynqajdkkkdntm




Cloudwatch Agent の Config Json を Ssm パラメータストアに移行する サーバーワークスエンジニアブログ




Building Amis Packer And Image Builder Kubes Clouds




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog



Aws Secure Access Infrastructure Identity Workshop 02 Using Aws Systems Manager Session Manager Md At Master Aws Samples Aws Secure Access Infrastructure Identity Workshop Github
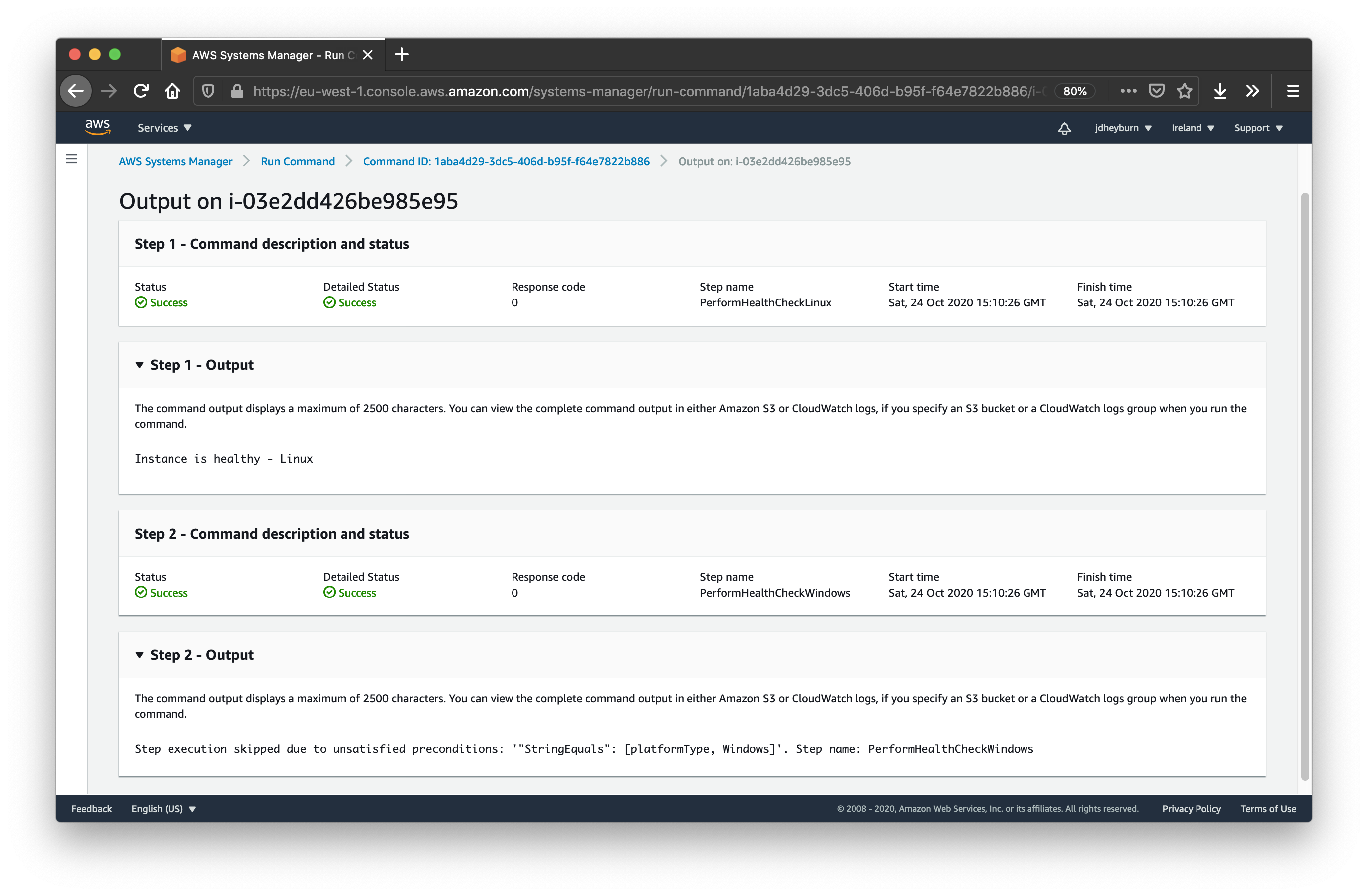



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn




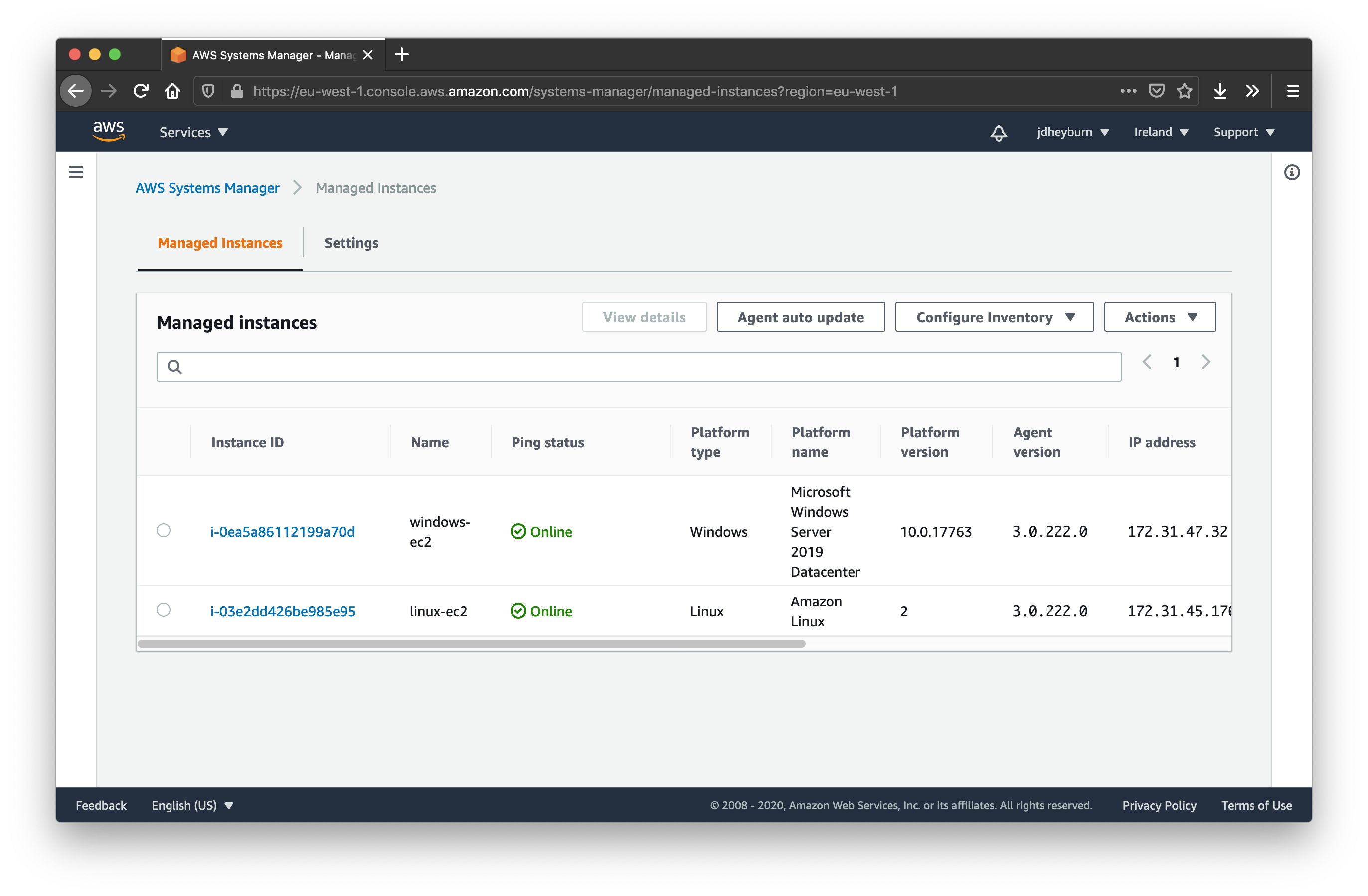
Ec2 Instance Doesn T Show Up In Aws Systems Manager Server Fault
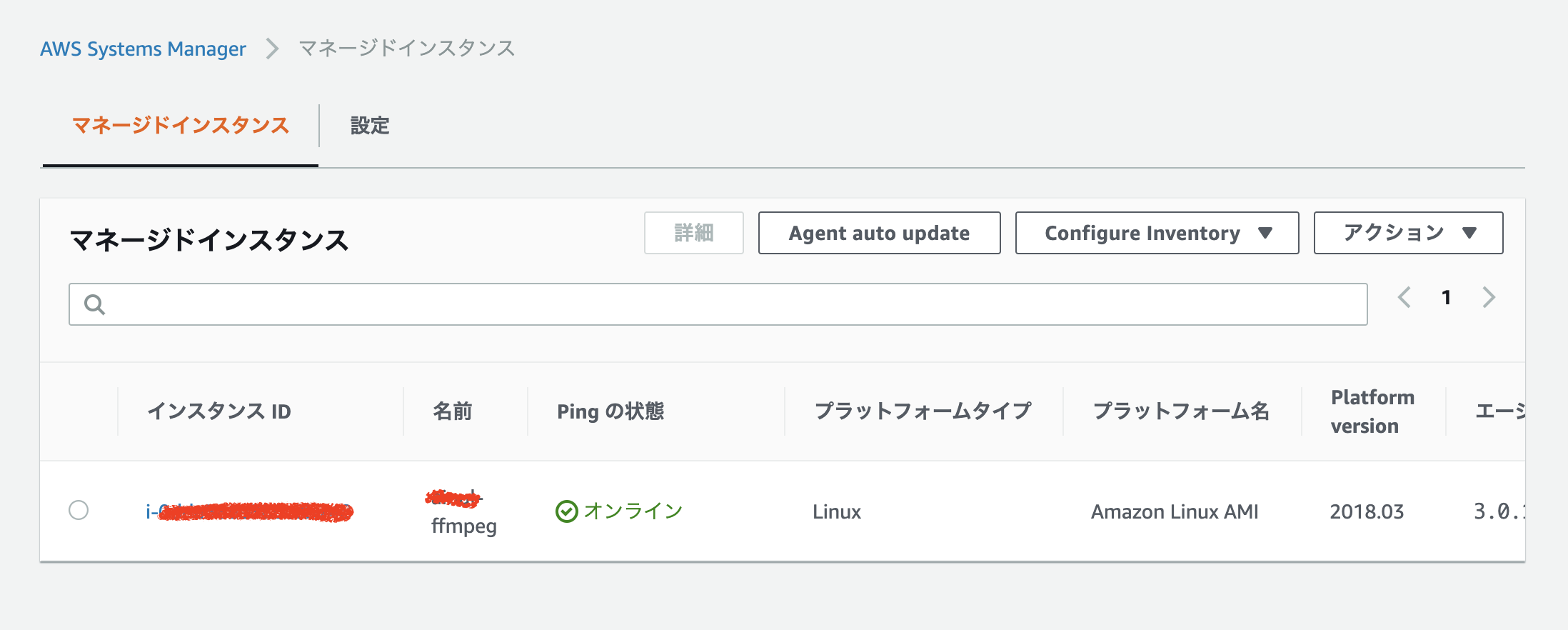



Aws Systems Managerを用いてec2上のコマンドを動かしてみた Qiita



Aws Quickstart Quickstart Eks Cdk Python Githubmemory




Substitute Your Ssh Bastions Using Aws Systems Manager




How To Achieve A Secure Connection To Ec2 Virtual Servers With Session Manager Without The Need Of Encryption Keys Financial Solutions




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog
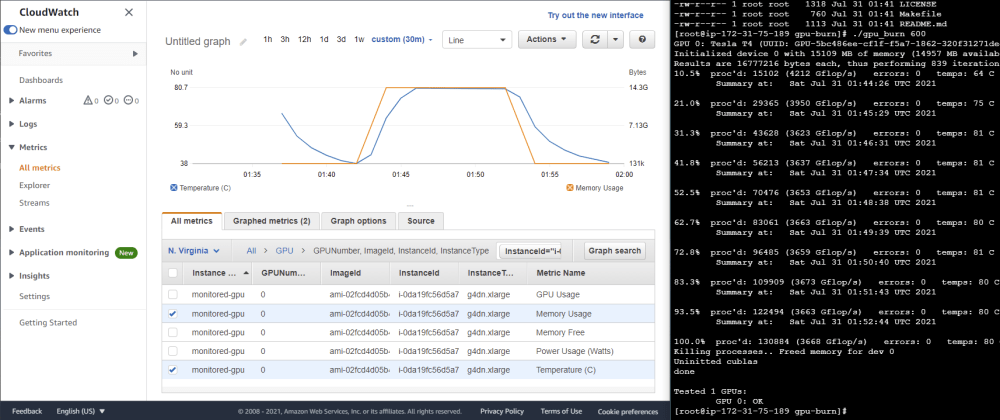



Instrumenting Amis For Gpu Monitoring On Cloudwatch Dev Community
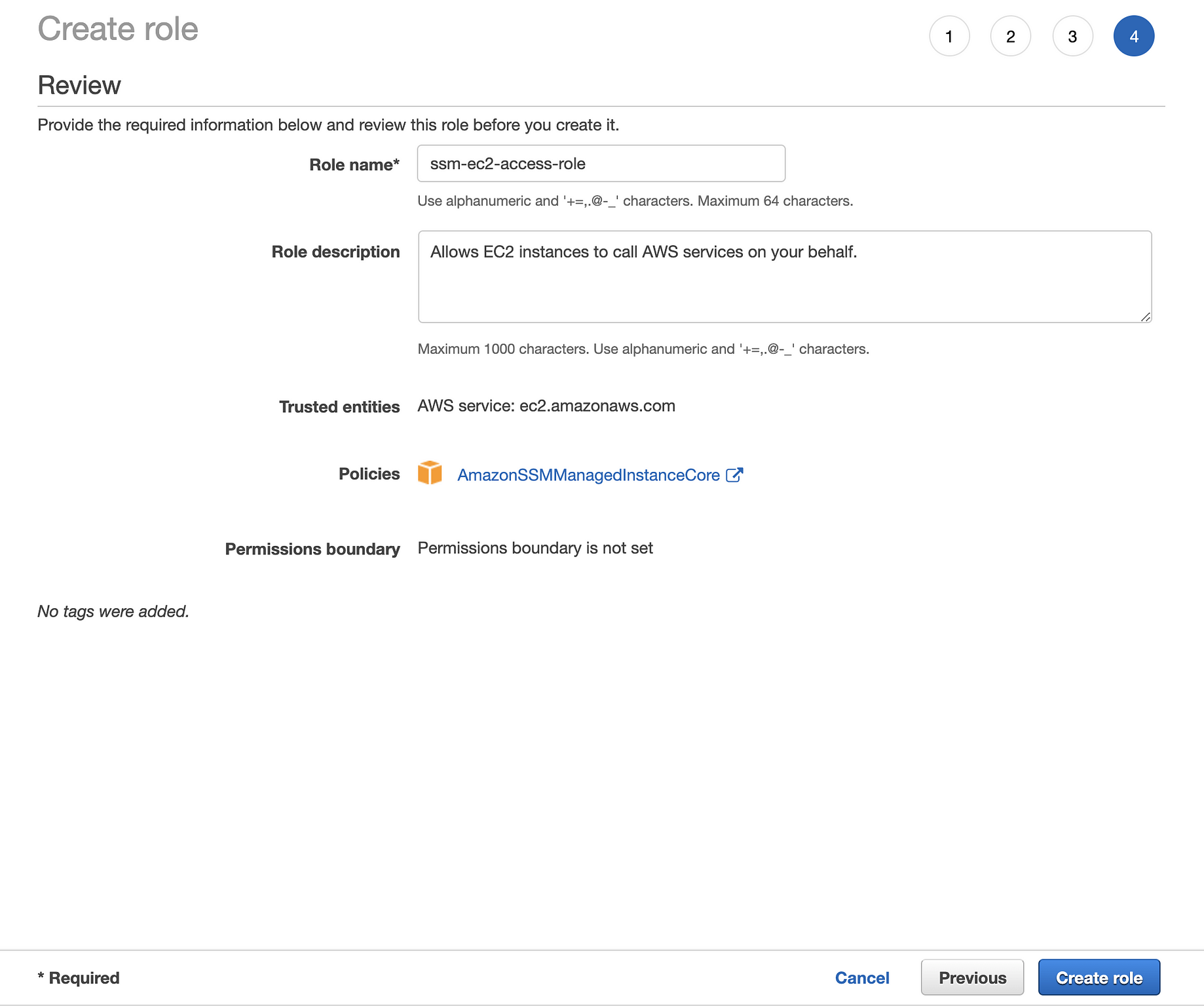



How To Connect An Ec2 Instance Via Systems Manager By Mert Saygi Medium
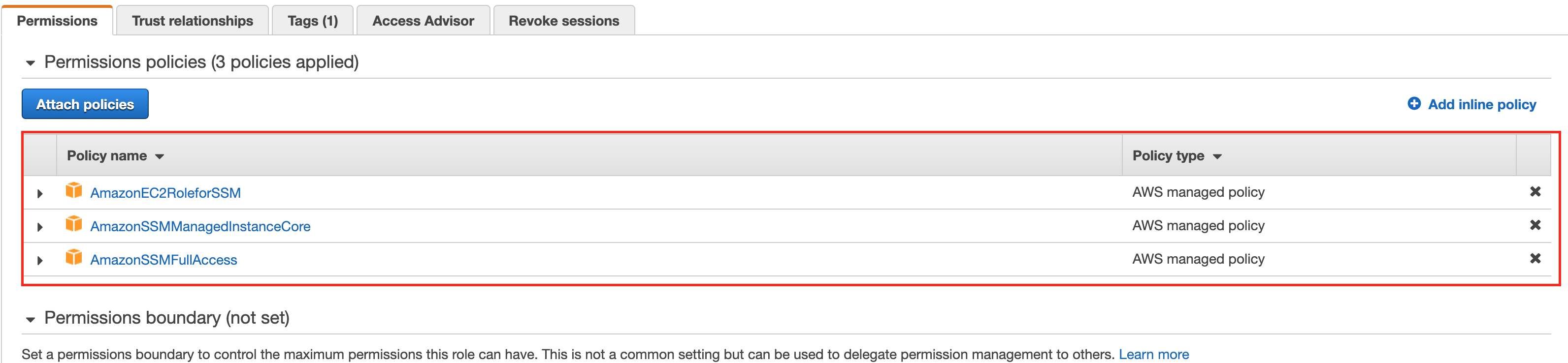



How To Provision Aws Ec2 In Private Subnet By Using Ssm And Ansible Dynamic Inventory Ru Rocker




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com




Improve Monitoring Of Aws Systems Manager Agent Aws Management Governance Blog



Github Siyer2 Sophon Server




Migrating Your On Premises Sql Server Windows Workloads To Amazon Ec2 Linux Aws Database Blog




Slice Engineering Makers Of Slice
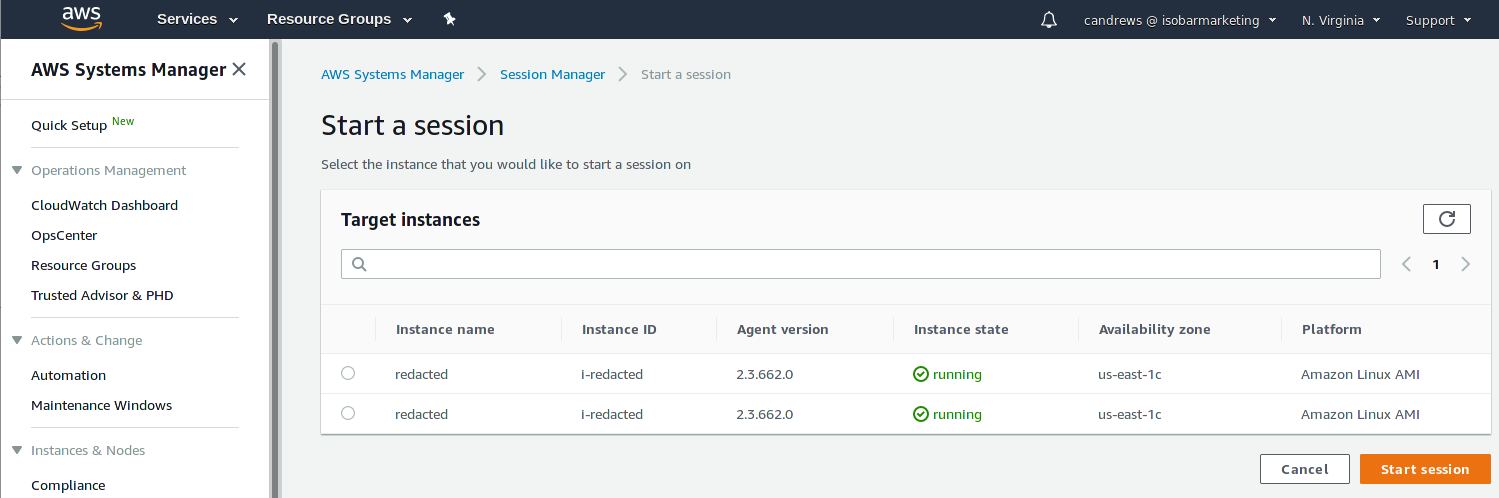



Improve Security And Reduce Costs With Aws Ssm Session Manager Craig Andrews




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Stack Over Cloud




Using Aws Systems Manager Session Manager Kernel Talks




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog




How To Add An Ec2 Instance To Aws System Manager Ssm Cloudaffaire




Run Ssh And Scp With Aws Session Manager Terrence Miao S Adventures




Slice Engineering Makers Of Slice
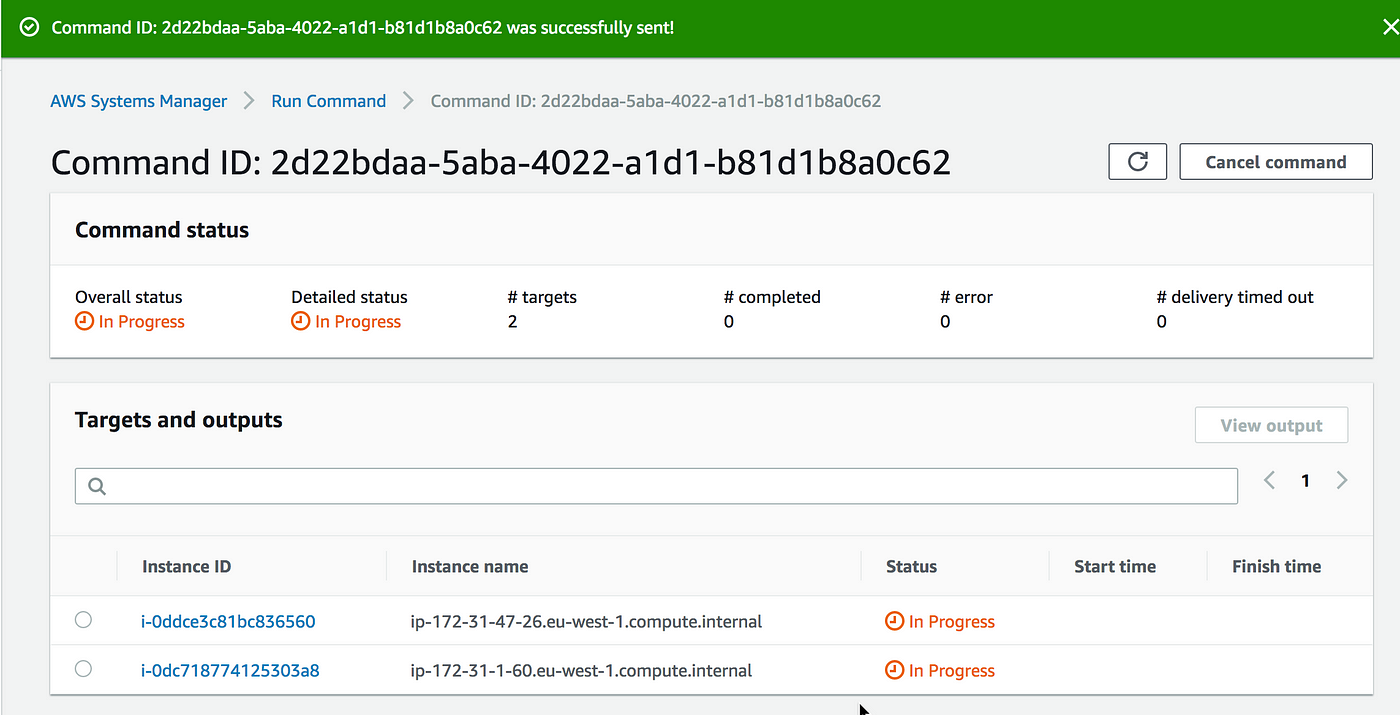



Chaos Engineering On Amazon Ec2 Using Aws System Manager Ssm The Cloud Architect
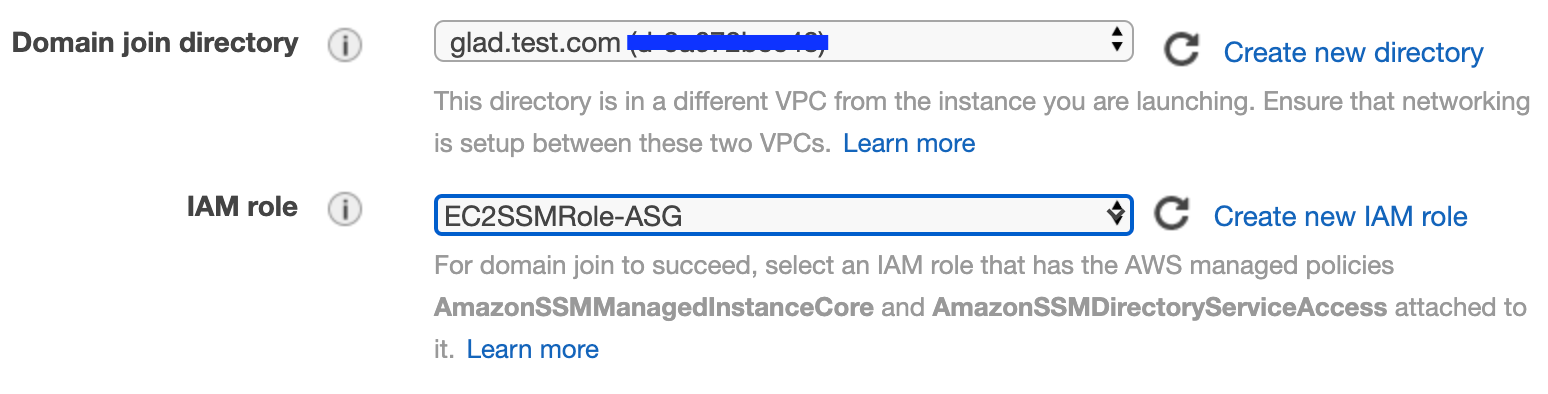



How To Join And Unjoin Aws Ec2 In Asg With Aws Directory Service By Surbhi Nijhara Medium




Slice Engineering Makers Of Slice
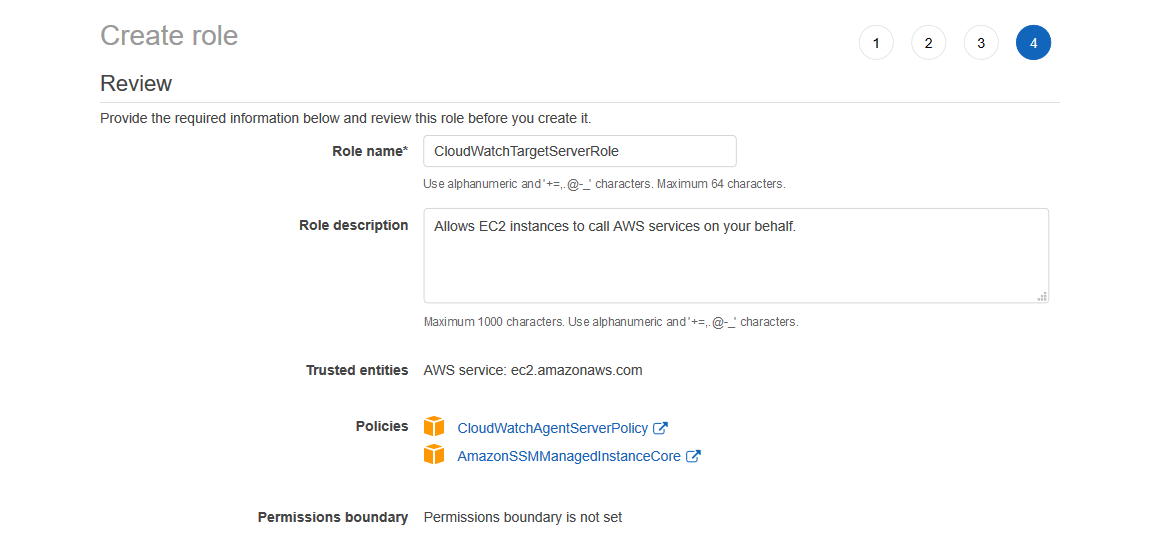



Export Ec2 Logs To Cloudwatch I Was Recently Tasked With Finding A By Omar Dulaimi Medium




Ec2 Instance Doesn T Show Up In Aws Systems Manager Server Fault




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com
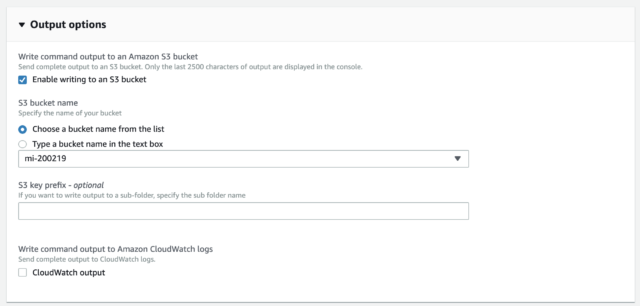



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio
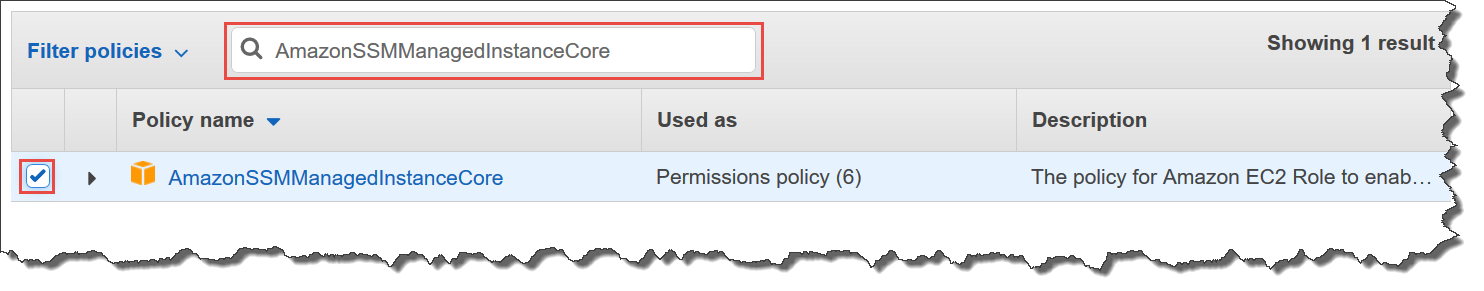



Step 4 Create An Iam Instance Profile For Systems Manager Aws Systems Manager




Shipping Aws Ec2 Logs To Cloudwatch With The Cloudwatch Agent Tom Gregory



Aws Big Data Noise Page 2



Flatcar Ssm Iam Tf At Master Surajnarwade Flatcar Ssm Github




Using Aws Systems Manager Run Command To Submit Spark Hadoop Jobs On Amazon Emr Aws Management Governance Blog
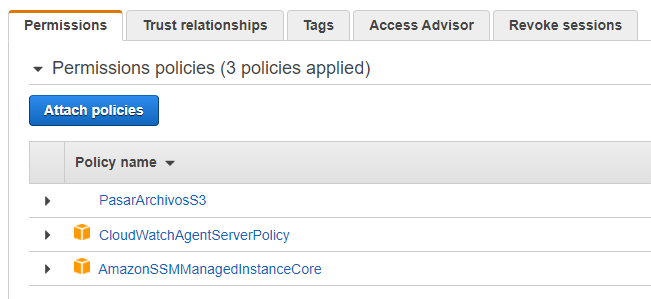



How To Achieve A Secure Connection To Ec2 Virtual Servers With Session Manager Without The Need Of Encryption Keys Financial Solutions




Stop Exposing Port 22 To The World It S Time To Rework Your Remote Access Methods Toolr Io




Shipping Aws Ec2 Logs To Cloudwatch With The Cloudwatch Agent Tom Gregory




Backup And Recovery Of Sap Hana Database Directly To Aws S3 Bucket Using Aws Backint Agent Part I
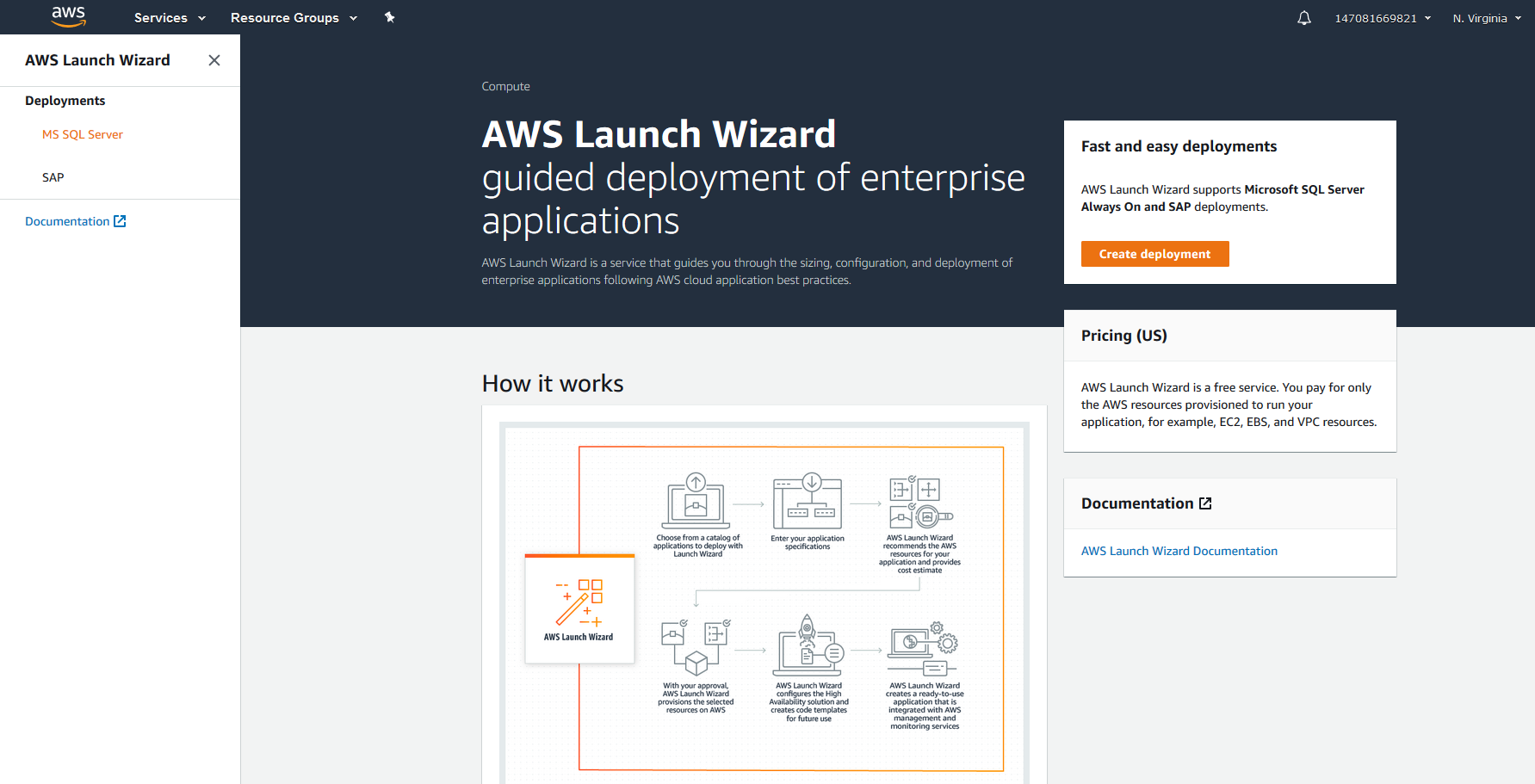



Aws Launch Wizard For Quick Sql Server Always On Deployments



Monitoring Ram Memory On Aws Ec2 Windows 19 Server With Cloudwatch And Ssm By Ziwon Kim Medium



Injecting Chaos To Amazon Ec2 Using Aws System Manager




Aws Ecs White Paper Pdf Amazon Web Services Computer Data




Slice Engineering Makers Of Slice




Ssh Logging And Session Management Using Aws Ssm Toptal




Instrumenting Amis For Gpu Monitoring On Cloudwatch Dev Community




新ポリシー Amazonssmmanagedinstancecore がサポートされました Developersio



Injecting Chaos To Amazon Ec2 Using Aws System Manager




Aws Launch Wizard For Quick Sql Server Always On Deployments




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise



Monitoring Ram Memory On Aws Ec2 Windows 19 Server With Cloudwatch And Ssm By Ziwon Kim Medium




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com



Cloud Watch에서 Ec2 메모리 모니터링 Ninano Tech Blog




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog




Securing Access To Emr Clusters Using Aws Systems Manager Aws Big Data Blog




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Stack Over Cloud



Reference And Import Existing Assets Into Aws Cdk The Devs In The Shed Blog
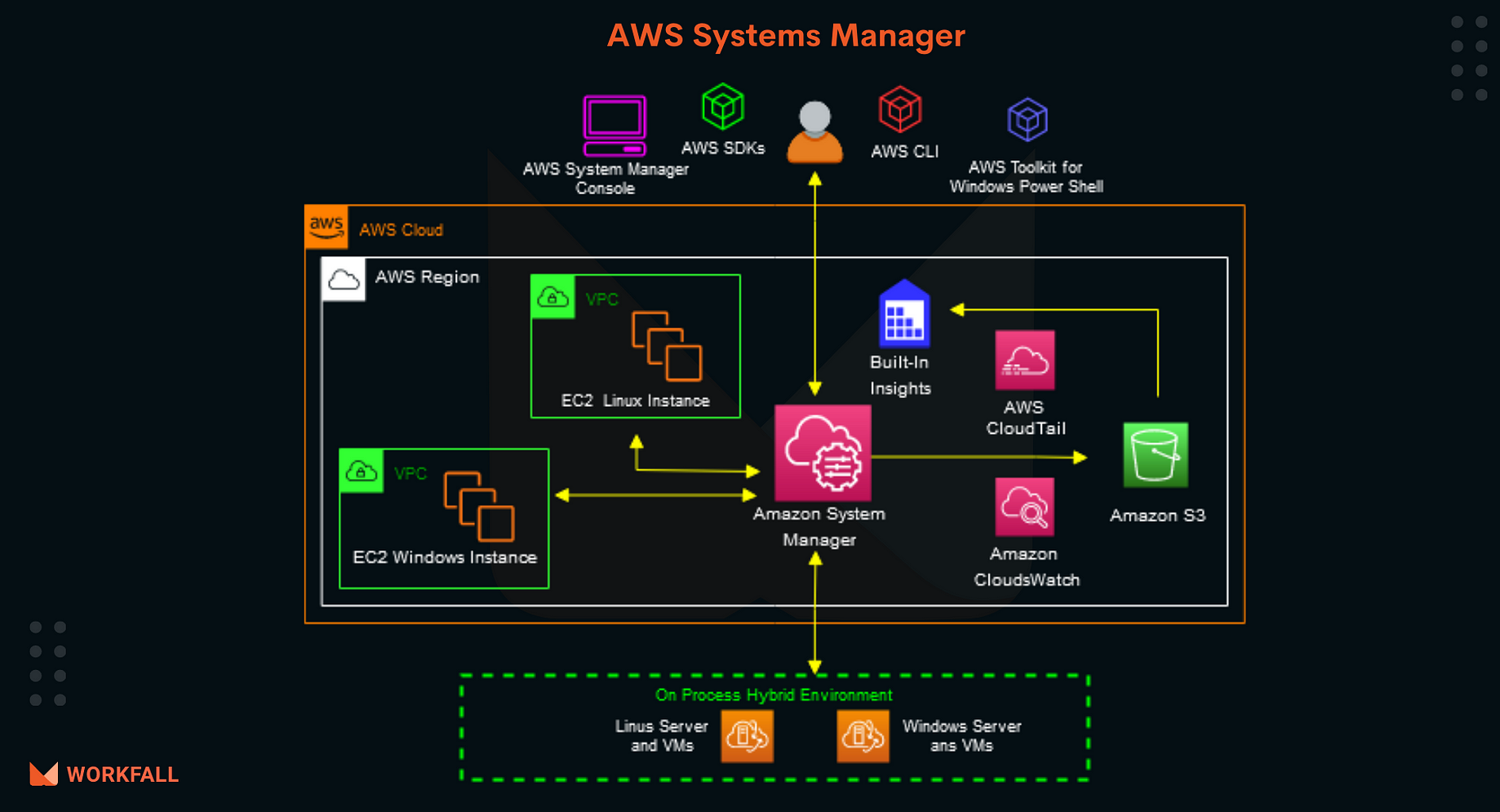



How To Run Commands Remotely On An Ec2 Instance Using Aws Systems Manager By Workfall The Workfall Blog Medium




Improve Monitoring Of Aws Systems Manager Agent Cloudpro Exam Prep
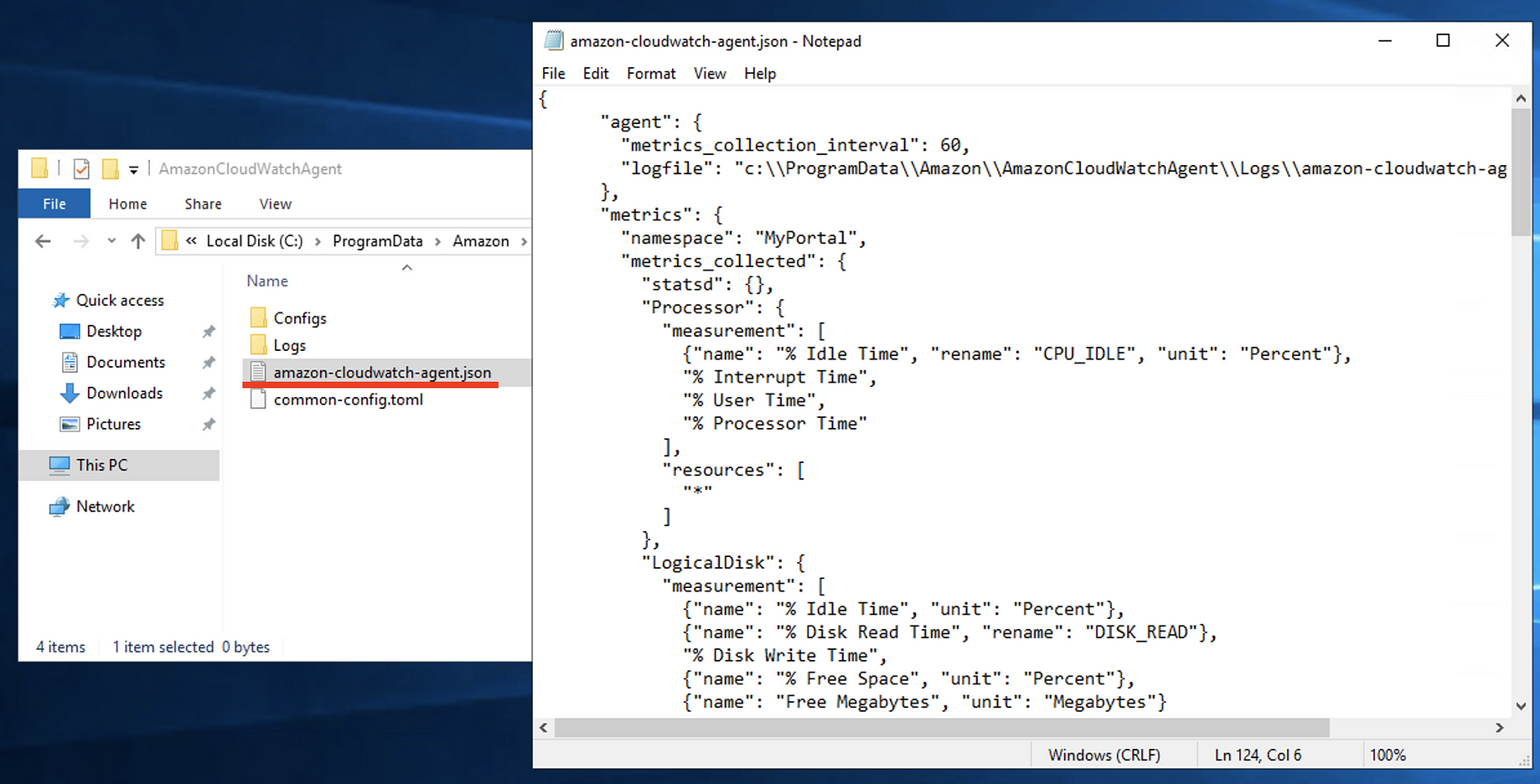



Monitoring Ram Memory On Aws Ec2 Windows 19 Server With Cloudwatch And Ssm By Ziwon Kim Medium




Aws Compute Optimizer にメモリのメトリクスを含める方法 サーバーワークスエンジニアブログ



Amazon Ssm Agent Githubmemory



Gnaf Template Yaml At Master Data61 Gnaf Github




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise



0 件のコメント:
コメントを投稿